Do you want to know the scariest part? Cybercriminals don’t even need to steal your phone to gain access to your number and personal information. This recent trend in hacking has become known as SIM card swapping.
Let’s take a closer look at what SIM card swapping is, and how you can avoid it.
How Does a SIM Card Work?
Before we dive into the nitty-gritty of the SIM swapping fraud, you’ll need to know how a SIM card works. Do you remember when you purchased your last phone? You might’ve noticed that one of your carrier’s representatives swapped your SIM card from your old phone to your new one.

Believe it or not, that tiny chip in your phone stores all of your essential account information. When its 20-digit ICCID number falls into the hands of a skilled criminal, you’re in trouble.
Advertisement
What Is the SIM Card Swapping Scam?
SIM card swapping involves a lot of trickery and deception. Hackers contact your service providers and hope to speak with an especially trusting employee. They’ll impersonate you to get what they want: your SIM card data.
If their scam is successful, your SIM card data will transfer to the criminal’s SIM card. No, they aren’t interested in your text messages or phone calls from your friends; they’re focused on receiving two-factor authentication (2FA) messages from accounts that hold your valuable information.
Most banks require 2FA when you sign in to your online account. But instead of you inputting the one-time password (OTP) received through SMS, the hacker does.
Tips to Protect Yourself From SIM Card Swapping
While there’s not much you can do once a hacker gets hold of your SIM card information, there are still methods you can use to prevent it from happening. Here are some of the most effective ways to halt hackers:
Advertisement
1. Change Your 2FA Method
Receiving your 2FA through text messages is convenient and all, but it can only make your situation worse when you’re a victim of SIM card swapping.
Opting to use an authenticator app like Authy or Google Authenticator associates your OTP with your actual phone, rather than your phone number. Simply connect the app to your most important accounts and you’ll receive your security codes through the app instead.
Set Up a PIN with Your Mobile Carrier
Adding a PIN to your account makes it harder for a hacker to gain access to it. A SIM swapper will have to provide your secret PIN or passcode when trying to make changes to your account, and that’s why it’s so important to have one.
Fortunately, you can add a PIN to your account by visiting your carrier’s website.
If you’re a customer at Verizon, you’re required to have a PIN. To edit or add a PIN to your account, sign in to your account Verizon’s PIN management page. After you determine your PIN, re-type it, then hit Submit.
To create a PIN on T-Mobile, sign in to your My T-Mobile account. You’ll have to pick a verification method and hit Select. Once this is complete, enter your PIN code, and click Next to confirm.
With AT&T, you can add a passcode to your account by signing in, and going to your Profile. Under Wireless passcode, hit Manage extra security. Clicking the checkbox will require you to provide a passcode when making major changes.
You can add a PIN from the Sprint website by signing in to your account, and selecting My Sprint. Click Profile and security, then locate the Security information section. Simply add or edit your PIN, and hit Save.
3. Separate Your Phone Number From Your Accounts
Have you ever used your phone as a way to change your password? When hackers steal your SIM card data, they can too.
Once hackers have locked you out of your own accounts, they’ll gather as much information as they can. Criminals won’t hesitate to take money out of your bank account, or even worse, sell your personal information on the dark web.
Deleting your phone number from your most important online accounts can save you the headache of worrying about a SIM card swap. If you’re required to have a phone number associated with your account, get a VoIP number with Google Voice instead.
4. Use Encrypted Messaging
SMS doesn’t support encryption, which means that hackers can easily spy on your messages and steal your 2FA codes. Using an encrypted messaging app such as iMessage, Signal, or WhatsApp can prevent nosy hackers.
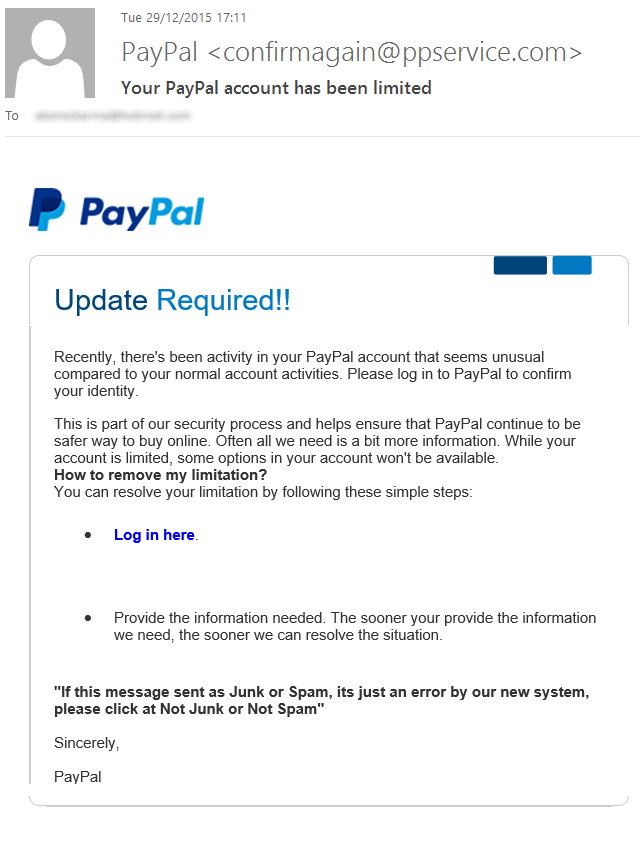
5. Beware of Phishing Scams
You should always delete sketchy emails that ask for your personal information. Banks and other institutions will never request confidential information via email. These types of emails are always a result of a hacker trying to steal your information.
Are You a Victim of SIM Swapping?
Many victims don’t realize they’ve been SIM swapped until it’s too late. The biggest warning sign of the fraud is a loss of cell reception.
Some banks and mobile carriers have security measures that prevent SIM card swapping from happening in the first place. Your carrier may let you know if your SIM card has been re-issued, while banks will usually send you an alert if it detects unusual activity on your account.
Having your mobile number attached to your accounts makes signing in simple. However, you can’t always count on your phone number staying safe forever. SIM card swapping poses too much of a threat to guarantee your privacy.
Be on the lookout for phishing emails, as answering those malicious inquiries can make a hacker’s job easy. Don’t know what a phishing email looks like? You can find more information in our article on how to spot a phishing email.
Image Credit: VitalikRadko/Depositphotos
Adding a PIN to your account makes it harder for a hacker to gain access to it. A SIM swapper will have to provide your secret PIN or passcode when trying to make changes to your account, and that’s why it’s so important to have one.
Fortunately, you can add a PIN to your account by visiting your carrier’s website.
If you’re a customer at Verizon, you’re required to have a PIN. To edit or add a PIN to your account, sign in to your account Verizon’s PIN management page. After you determine your PIN, re-type it, then hit Submit.
To create a PIN on T-Mobile, sign in to your My T-Mobile account. You’ll have to pick a verification method and hit Select. Once this is complete, enter your PIN code, and click Next to confirm.
With AT&T, you can add a passcode to your account by signing in, and going to your Profile. Under Wireless passcode, hit Manage extra security. Clicking the checkbox will require you to provide a passcode when making major changes.
You can add a PIN from the Sprint website by signing in to your account, and selecting My Sprint. Click Profile and security, then locate the Security information section. Simply add or edit your PIN, and hit Save.
3. Separate Your Phone Number From Your Accounts
Have you ever used your phone as a way to change your password? When hackers steal your SIM card data, they can too.
Once hackers have locked you out of your own accounts, they’ll gather as much information as they can. Criminals won’t hesitate to take money out of your bank account, or even worse, sell your personal information on the dark web.
Deleting your phone number from your most important online accounts can save you the headache of worrying about a SIM card swap. If you’re required to have a phone number associated with your account, get a VoIP number with Google Voice instead.
To delete your phone number from Google, sign in to the Google Account page and head to the Personal Info section. If you see your phone number, make sure to delete it.
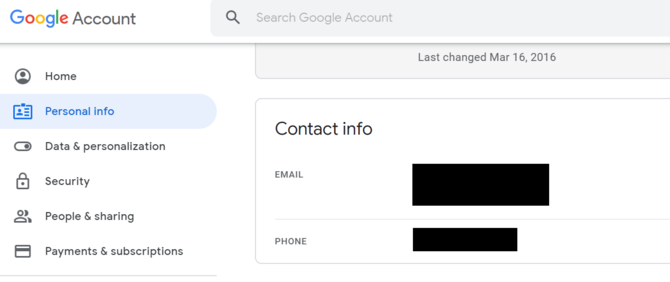
In the Security section, scroll down, and remove your phone number from the Ways we can verify it’s you option.
For Amazon, click Your Account, and then navigate to Login & Security. Erase your phone number or add a VoIP number from there.
You can also erase your phone number from PayPal by clicking the gear icon in the corner of the web page. Under the Phone section, choose to change your number.

You should also erase your phone number on major social media sites, online retailers, and especially your online banking account.

In the Security section, scroll down, and remove your phone number from the Ways we can verify it’s you option.

For Amazon, click Your Account, and then navigate to Login & Security. Erase your phone number or add a VoIP number from there.

You can also erase your phone number from PayPal by clicking the gear icon in the corner of the web page. Under the Phone section, choose to change your number.

You should also erase your phone number on major social media sites, online retailers, and especially your online banking account.
4. Use Encrypted Messaging
SMS doesn’t support encryption, which means that hackers can easily spy on your messages and steal your 2FA codes. Using an encrypted messaging app such as iMessage, Signal, or WhatsApp can prevent nosy hackers.
5. Beware of Phishing Scams
You should always delete sketchy emails that ask for your personal information. Banks and other institutions will never request confidential information via email. These types of emails are always a result of a hacker trying to steal your information.
Are You a Victim of SIM Swapping?
Many victims don’t realize they’ve been SIM swapped until it’s too late. The biggest warning sign of the fraud is a loss of cell reception.
Some banks and mobile carriers have security measures that prevent SIM card swapping from happening in the first place. Your carrier may let you know if your SIM card has been re-issued, while banks will usually send you an alert if it detects unusual activity on your account.
Having your mobile number attached to your accounts makes signing in simple. However, you can’t always count on your phone number staying safe forever. SIM card swapping poses too much of a threat to guarantee your privacy.
Be on the lookout for phishing emails, as answering those malicious inquiries can make a hacker’s job easy. Don’t know what a phishing email looks like? You can find more information in our article on how to spot a phishing email.
Image Credit: VitalikRadko/Depositphotos